For several years, the Internet Engineering Task Force (IETF) has been working to improve the Transport Layer Security (TLS) protocol, which is designed to help developers protect data as it moves around the internet. Facebook created an API library called Fizz to enhance the latest version, TLS 1.3, on Facebook’s networks. Today, it announced it’s open sourcing Fizz and placing it on GitHub for anyone to access and use.
Facebook is currently running more than 50 percent of its traffic through TLS 1.3 and Fizz, which they believe is the largest implementation of TLS 1.3 to date.
All of this is referring to how traffic moves around the internet and how servers communicate with one another in a secure way. This is particularly important because as Facebook points out, in modern internet server architecture, it’s not uncommon to have different key pieces of the process spread out across the world. This raises challenges around reducing latency as data moves from server to server.
One of the major issues involved writing data to a huge chunk of memory, which increased resource overhead and reduced speed. To get around this issue, Facebook decided to divide the data into smaller chunks as it moved into memory and then encrypt it in place, a process called scatter/gather I/O. This provides a more efficient way of processing data in memory, reducing the overhead required to process it, while increasing the processing speed.
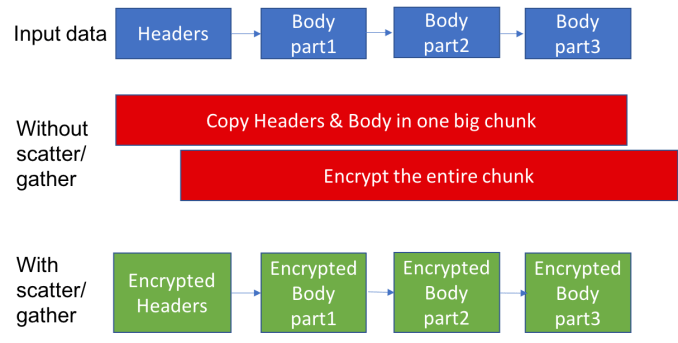
Instead of encrypting a single of chunk of data, using Scatter/Gather Fizz breaks it into discrete pieces and encrypts each one. Diagram: Facebook.
TLS 1.3 introduced a concept called “early data” (also known as zero round trip data or 0-RTT data), which has helped reduce latency. According to ITEF, it does this by “allowing a client to send data to a server in the first round trip of a connection, without waiting for the TLS handshake to complete if the client has spoken to the same server recently.” The problem is that this concept can be insecure, so Fizz includes APIs that support this concept and builds on it by reducing the known vulnerabilities.
The company has been working with IETF because it has unique needs due to the sheer number of transactions it processes on a daily basis. According to Facebook, TLS 1.3, “incorporates several new features that make internet traffic more secure, including encrypting handshake messages to keep certificates private, redesigning the way secret keys are derived, and a zero round-trip connection setup, which makes certain requests faster than TLS 1.2.”
As for Fizz, “In addition to the enhancements that come with TLS 1.3, Fizz offers an improved solution for middlebox handshake failures, supports asynchronous I/O by default, and can handle scatter/gather I/O to eliminate the need for extra copies of data,” Facebook wrote in the blog post announcing it was open sourcing the library.
Fizz improves the newest version of the Transport Layer Security protocol, and by making it open source, Facebook is sharing this technology with the community at large where others can take advantage of and build upon the work Facebook has done.